
Almost every day, thousands of attacks successfully executed towards the organization of all sizes. But yet many victims had the best endpoint protection solution in place.
If the adoption of antivirus is universal, why there are so many attacks reported every day?
In general, hackers expect the targets to be running some form of endpoint antivirus protection. They keep on adapted their procedure, tools and techniques to bypass the detection and to compromise further.
There is a large number of opportunities to bypass traditional protection from sophisticated morphism and obfuscation of malware to malicious usage of legitimate applications or even a straightforward credential theft.
Conventional antivirus that focuses primarily on detecting and preventing known malware on signature-based detection is not capable of managing this new generation of rapidly evolving threats.
Hence, the increasing number of organizations are looking for solutions that can effectively handle these emerging challenges.
You could think about the Zero-day attack, for example.

With so many options and so much hype, finding the right solution can often seem quite tricky and even challenging for some people.
Here are some factors for you to consider when finding the best endpoint protection for your organization.
Considering that new threats emerge continuously, a good antivirus must able to recognizes and protects your computer and network-based signature that been updated regularly on the latest threats.
Zero-day threats released into the wild before security vendors can issue protection against them.
Usually, on Microsoft Software, attackers take advantage of Microsoft monthly security update cycle, and new attack created just before the next patch.
Malicious programs can attack by targeting unpatched vulnerabilities in your operating system and applications until security software companies become aware of it.
Attackers can use trusted Windows processes to execute exploits, knowing that they will almost certainly evade traditional endpoint security measures such as antivirus and whitelisting.
This includes both PowerShell and Windows Management Instrumentation (WMI). An endpoint protection solution requires complete exploit blocking for attacks such as ASLR, Buffer Overflows and others to stop the attacks.
You need visibility into what users are doing on their endpoints, what’s happening with the files located there, and where that endpoint is trying to connect to on the internet.
Look for solutions that can protect your corporate devices wherever they are.
3rd parties like AV-Test, NSS Labs, or Gartner will cover the result of market and research to help customers in their decision making. Make use of the reports to make your decision on choosing the best platform.
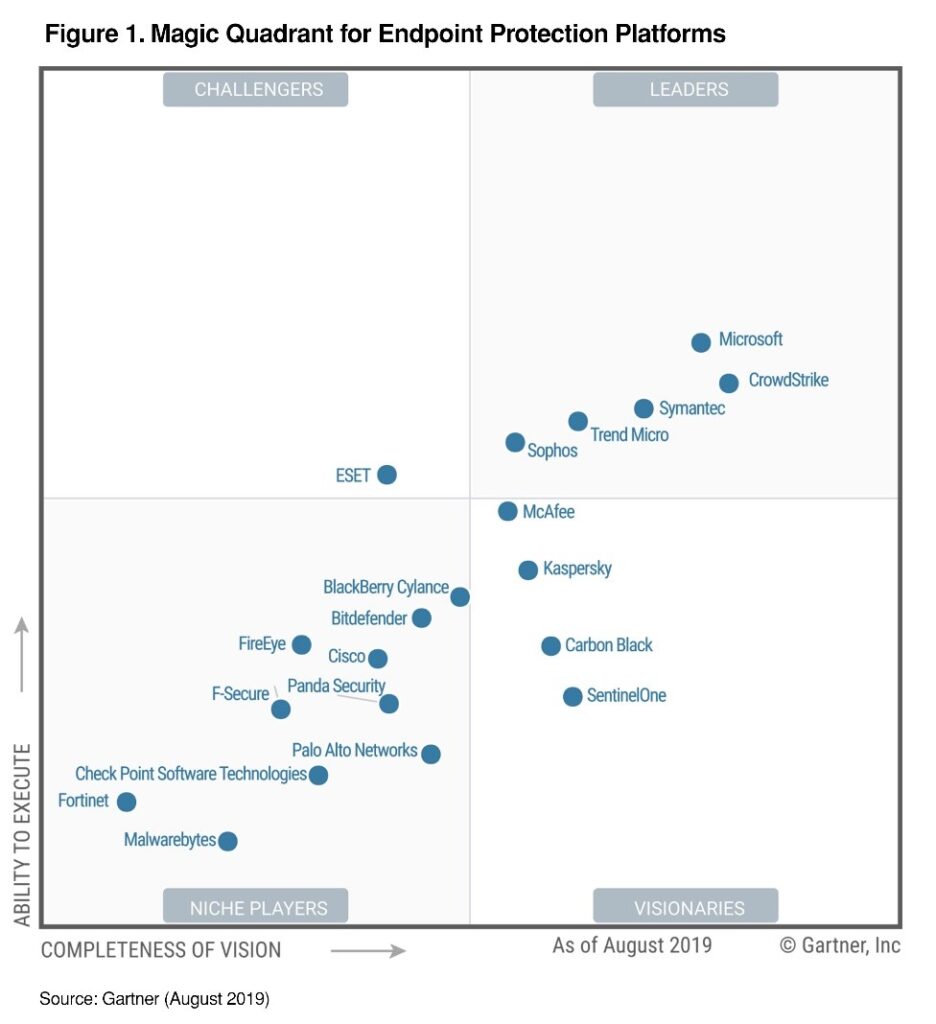
To further measure Endpoint protection products, we have to understand several functionalities, and IT features.
Traditional AV/ Signature Based - Old technology
Machine Learning - uses algorithms and math's to detect an attack.
Sandboxing - Isolated to analyze behaviour mostly runs as virtual machines
Exploits Prevention or blocking - able to block both signatures and unknown
Enterprise Detection and Response - monitors, responds and investigate to mitigate cyber threats
In my next post, I will share more about Endpoint Protection for you to learn.